In another post I already outlined the installation and setup of an OpenVPN server in my Oracle Cloud Infrastructure (OCI). As a result, I was able to securely connect to my cloud resources from my laptop by establishing a VPN connection. Because my new router at home can now handle VPN connections on it’s own, I wanted to utilize this feature. At a first glance, an IPsec connection would be best. But at the OCI side I need to create a “Customer On-Prem Equipment” (CPE) which represents the peer that connects to OCI. But unfortunately this has to be an IP address rather than a name that can be resolved via DNS. Since my provider changes my IP from time to time, using IPsec is not really an option. That’s why I use OpenVPN instead.
In the previous post I used a configuration file along with separate files for the required keys and certificates. My router now requires a single .ovpn file. This file is quite easy to build, I found the answer on ServerFault which has a reference to the OpenVPN manuals. The basic idea is to include the keysand certificates in XML-style syntax to the config file:
INLINE FILE SUPPORT
OpenVPN allows including files in the main configuration for the –ca, –cert, –dh, –extra-certs, –key, –pkcs12, –secret and –tls-auth options.Each inline file started by the line <option> and ended by the line </option>
For my case I create the single configuration file as follows, assuming all the required files are in the same directory:
[root@dbamarco-01 ~]# cd /etc/openvpn/client/
[root@dbamarco-01 client]# ll
total 28
-rw-------. 1 root root 1212 Jun 23 18:18 ca.crt
-rw-r--r--. 1 root root 453 Jun 24 07:05 client.ovpn
-rw-r--r--. 1 root root 7945 Aug 8 12:24 client.ovpn.full
-rw-------. 1 root root 4534 Jun 23 18:18 dbamarco-client01.crt
-rw-------. 1 root root 1704 Jun 23 18:18 dbamarco-client01.key
[root@dbamarco-01 client]# (
> echo '<ca>'
> cat ca.crt
> echo '</ca>'
> echo '<cert>'
> cat dbamarco-client01.crt
> echo '</cert>'
> echo '<key>'
> cat dbamarco-client01.key
> echo '</key>'
> ) >> client.ovpn
The single configurationfile then looks like this (stripped key/certificate data):
[root@dbamarco-01 client]# cat client.ovpn
client
dev tun
proto udp
remote 287.387.10.1 1194 # obfuscated
ca ca.crt
cert dbamarco-client01.crt
key dbamarco-client01.key
;cipher AES-256-CBC
;auth SHA512
;auth-nocache
;tls-version-min 1.2
;tls-cipher TLS-DHE-RSA-WITH-AES-256-GCM-SHA384:TLS-DHE-RSA-WITH-AES-256-CBC-SHA256:TLS-DHE-RSA-WITH-AES-128-GCM-SHA256:TLS-DHE-RSA-WITH-AES-128-CBC-SHA256
resolv-retry infinite
compress lz4
nobind
persist-key
persist-tun
mute-replay-warnings
verb 3
<ca>
-----BEGIN CERTIFICATE-----
XXX
-----END CERTIFICATE-----
</ca>
<cert>
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
XXX
</cert>
<key>
-----BEGIN PRIVATE KEY-----
XXX
-----END PRIVATE KEY-----
</key>
In this file, I just changed the “remote” IP address to point to a DNS name, that I keep updated using my preferred dynamic DNS service. I can now configure my router using this file.
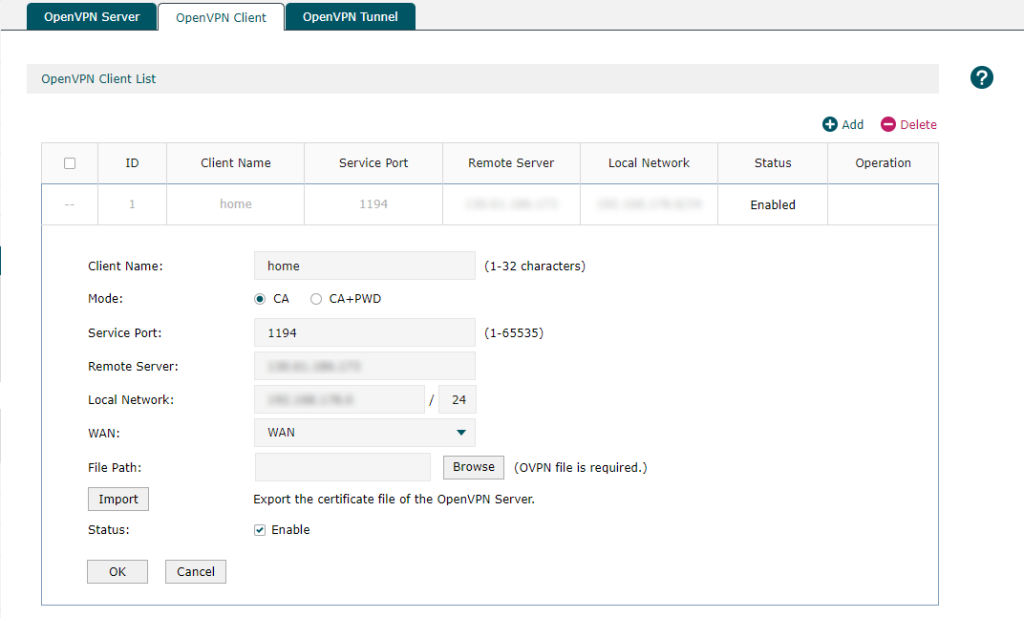
Here I use the configuration file and can then connect my router to the OCI.
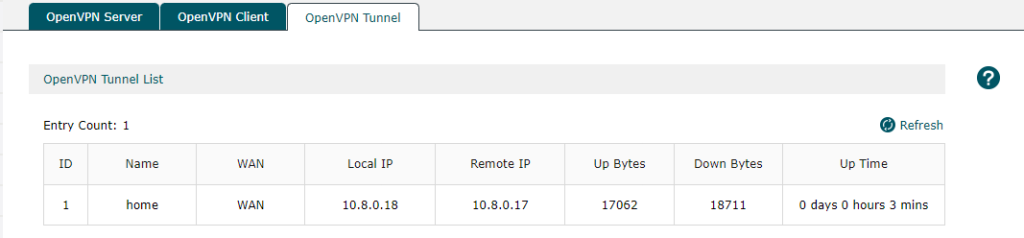
Once the connection is established, I can connect to my cloud resources using their private IP addresses. All the required routing and security is already set up.
Cool new router, that I have 🙂